Recently identified PDF encryption vulnerabilities
NewsOctober 8, 2019


NewsOctober 8, 2019

About PDF Association staff
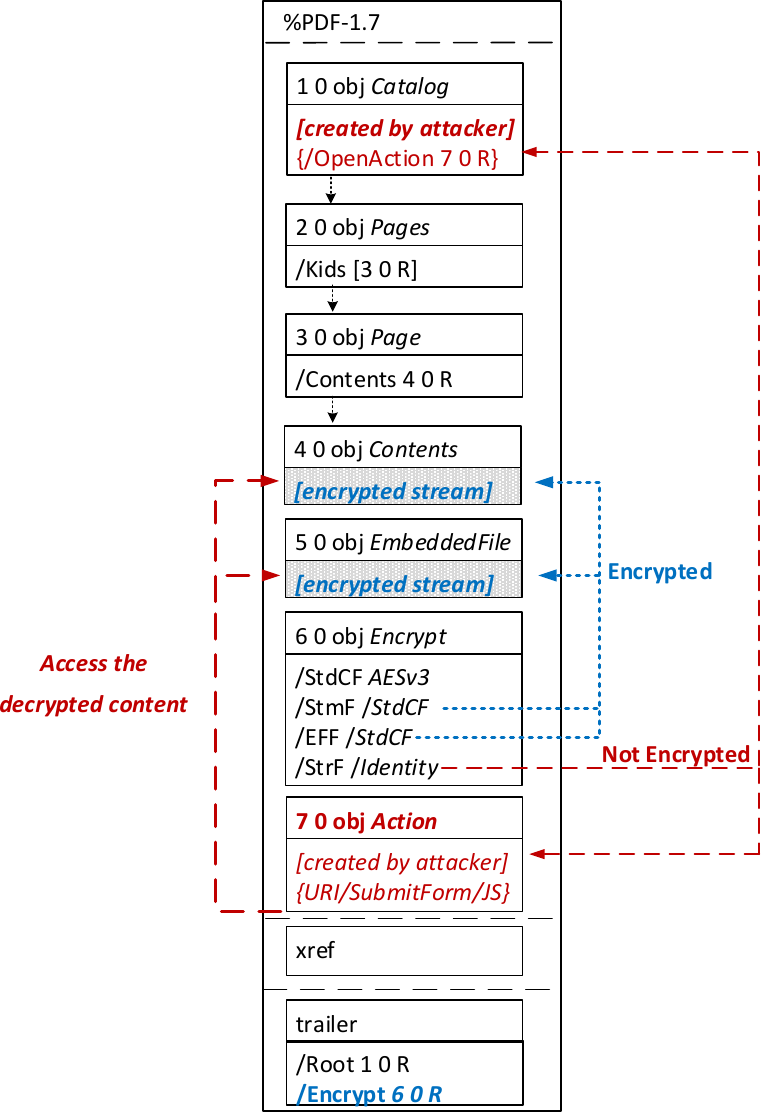
On September 30, 2019, a group of researchers from Ruhr University Bochum, FH Münster University of Applied Sciences, and Hackmanit GmbH published a new post discussing vulnerabilities identified in PDF viewers relevant to the use of encryption in PDF documents.
The vulnerabilities they identify are pertinent only to PDF files that require a password to open, and not PDF in general.
These vulnerabilities require an attacker to modify an encrypted PDF file, potentially leading to the exfiltration of the document's contents to an external server. This class of problem is not specific to PDF per se, but is applicable to most formats that support encryption.
It's important to recognize that not only PDF viewers, but potentially any PDF renderer supporting actions or JavaScript could be hijacked for malicious effect.
As is customary for responsible reporting of software vulnerabilities the research team says that it followed responsible reporting practices and has worked with vendors to address these issues before publishing the details of these vulnerabilities.
This post is intended to help ensure that the community is aware of the issue and to support all PDF developers in understanding how to identify and fix their software.
Mitigations
Update software. In most or all cases, vendors have already updated their software to guard against these attacks, but only users can ensure they are using the latest version.
Trust the sender. It's been a good general practice to only open attachments from trusted senders, regardless of format, for a long time, and that continues to be an effective mitigation in this case.
Manage the viewer. Set viewing software to require confirmation of form submission, following links and accessing external resources if the viewer supports these options.
Digitally-sign encrypted PDF files. Users can sign PDFs to reduce the degree of vulnerability. If the file has been changed the signature will be invalidated (assuming your software was previously updated to resolve the digital signature vulnerability identified by the same researchers earlier this year).
Use current-generation PDF software. Older software, especially unmaintained software, will remain vulnerable. Be sure to use PDF software that leverages the latest PDF specification and stays up-to-date with industry best practice.
In the ISO committee
The ISO committee responsible for PDF (ISO TC 171 SC 2 WG 8) is actively working on improving encryption and digital signature support in PDF. Given the wide adoption of PDF around the world in numerous industries, a “quick fix” (especially a fix that would be incompatible with existing implementations) is not in anyone’s interest.
Members of the PDF Association have access to the TC 171 SC 2 program, including draft documents and working group reports, and may use thePDF Association's Technical Working Groups to provide input or participate in technical discussions on this and related subjects.
Thanks to the researchers!
The PDF technology community expresses its thanks and appreciation to the researchers working at Ruhr University Bochum, FH Münster University of Applied Sciences, and Hackmanit GmbH for following best practice in alerting developers prior to publishing these vulnerabilities. Efforts such as theirs help make all users safer and more secure.




